
WordCloud representation of paper abstracts.
Research Interests
- Online privacy
- Network traffic analysis
- Privacy in IoT
- Privacy in Voice and VR interfaces
- Privacy-enhancing technologies
- Inference attacks
- Usable security and privacy
- Machine Learning+Privacy
- Anonymity networks
Research Topics
Security and Privacy in IoT
Today, with the rapid adoption of the Internet of Things (IoT), we face a new world where we are never alone. At all times, a plethora of connected devices, from smartphones to home assistants to motion detectors, sense and monitor our activities. While these devices provide us convenience, they are often backed by powerful analytics to sift through a large volume of personal data, at times collected without our awareness or consent. In my research, I look at developing novel frameworks that can discover, inform and control information flow. We are also looking at developing privacy-preserving techniques for different emerging IoT ecosystems.
Please visit our IoTLab page for more details on projects we are currently working on.
Relevant publications:
- "What are they gonna do with my data?": Privacy Expectations, Concerns, and Behaviors in Virtual Reality. Abhinaya S.B., Abhishri Agrawal, Yaxing Yao, Yixin Zou, and Anupam Das. Proceedings on Privacy Enhancing Technologies (PoPETs), 2025.
- Unveiling Users’ Security and Privacy Concerns Regarding Smart Home IoT Products from Online Reviews. Taufiq Islam Protick, Aafaq Sabir, S.B. Abhinaya, and Anupam Das. ACM Journal on Computing and Sustainable Societies, 2024.
- Detecting Smart Home Device Activities Using Packet-Level Signatures from Encrypted Traffic. Mohammad Shamim Ahsan, Md. Shariful Islam, Md. Shohrab Hossain, and Anupam Das. IEEE Transactions on Dependable and Secure Computing (TDSC), 2024.
- Understanding Parents’ Perceptions and Practices Toward Children’s Security and Privacy in Virtual Reality. Jiaxun Cao, Abhinaya S.B., Anupam Das and Pardis Emami-Naeini. Proceedings of the 45th IEEE Symposium on Security and Privacy (IEEE S&P), 2024.
- Enabling Developers, Protecting Users: Investigating Harassment and Safety in VR. Abhinaya S.B., Aafaq Sabir and Anupam Das. Proceedings of the 33rd USENIX Security Symposium (USENIX Security), 2024.
- Connecting the Dots: Tracing Data Endpoints in IoT Devices. Md Jakaria, Danny Yuxing Huang and Anupam Das. Proceedings on Privacy Enhancing Technologies (PoPETs), 2024.
- Spying through your voice assistants: Realistic voice command fingerprinting. Dilawer Ahmed, Aafaq Sabir and Anupam Das. Proceedings of the 32nd USENIX Security Symposium (USENIX Security), 2023.
- INSPIRE: Instance-level Privacy-preserving Transformation for Vehicular Camera Videos. Zhouyu Li, Ruozhou Yu, Anupam Das, Shaohu Zhang, Huayue Gu, Xiaojian Wang, Fangtong Zhou, Aafaq Sabir, Dilawer Ahmed and Ahsan Zafar. Proceedings of the 32nd International Conference on Computer Communications and Networks (ICCCN), 2023.
- VoicePM: A Robust Privacy Measurement on Voice Anonymity. Shaohu Zhang, Zhouyu Li and Anupam Das. Proceedings of the 16th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), 2023.
- Speaker Orientation-Aware Privacy Control to Thwart Misactivation of Voice Assistants. Shaohu Zhang, Aafaq Sabir and Anupam Das. Proceedings of the 53rd Annual IEEE/IFIP International Conference on Dependable Systems and Network (IEEE IFIP DSN), 2023.
- Heat Marks the Spot: De-Anonymizing User’s Geographical Data on the Strava Heatmap. Kevin Childs, Daniel Nolting and Anupam Das. 7th Workshop on Technology and Consumer Protection (ConPro), 2023.
- MetaMorphosis: Task-oriented Privacy Cognizant Feature Generation for Multi-task Learning. Md Adnan Arefeen, Zhouyu Li, Md Yusuf Sarwar Uddin and Anupam Das. Proceedings of the 8th ACM/IEEE Conference on Internet of Things Design and Implementation (IoTDI), 2023.
- Hey Alexa, Who Am I Talking to?: Analyzing Users’ Perception and Awareness Regarding Third-party Alexa Skills. Aafaq Sabir, Evan Lafontaine and Anupam Das. Proceedings of the 2022 ACM Conference on Human Factors in Computing Systems (CHI) , 2022.
- Analyzing the Feasibility and Generalizability of Fingerprinting Internet of Things Devices. Dilawer Ahmed, Anupam Das and Fareed Zaffar. Proceedings on Privacy Enhancing Technologies (PoPETs), 2022.
- HandLock: Enabling 2-FA for Smart Home Voice Assistants using Inaudible Acoustic Signal. Shaohu Zhang and Anupam Das. International Symposium on Research in Attacks, Intrusions and Defenses (RAID), 2021.
- Understanding People's Attitude and Concerns towards Adopting IoT Devices. Evan Lafontaine, Aafaq Sabir, and Anupam Das. CHI Conference on Human Factors in Computing Systems Extended Abstracts (CHI ’21 Extended Abstracts), 2021.
- Hey Alexa, is this Skill Safe?: Taking a Closer Lookat the Alexa Skill Ecosystem. Christopher Lentzsch, Sheel Jayesh Shah, Benjamin Andow, Martin Degeling, Anupam Das and William Enck. Network and Distributed System Security Symposium (NDSS), 2021.
- ''Did you know this camera tracks your mood?'': Understanding Privacy Expectations and Preferences in the Age of Video Analytics. Shikun Zhang, Yuanyuan Feng, Lujo Bauer, Lorrie Cranor, Anupam Das and Norman Sadeh. Proceedings on Privacy Enhancing Technologies (PoPETs), 2021.

- Enabling Live Video Analytics with a Scalable and Privacy-Aware Framework. Junjue Wang, Brandon Amos, Anupam Das, Padmanabhan Pillai, Norman Sadeh and Mahadev Satyanarayanan. ACM Transactions on Multimedia Computing, Communications, and Applications (TOMM), 2018.
- Personalized Privacy Assistants for the Internet of Things: Providing Users with Notice and Choice. Anupam Das, Martin Degeling, Daniel Smullen and Norman Sadeh. IEEE Pervasive Computing: The Spectre of Malicious Computing, 2018.
- A Scalable and Privacy-Aware IoT Service for Live Video Analytics. Junjue Wang, Brandon Amos, Anupam Das, Padmanabhan Pillai, Norman Sadeh and Mahadev Satyanarayanan. ACM Multimedia Systems Conference (MMSys), 2017.

- Some Recipes Can Do More Than Spoil Your Appetite: Analyzing the Security and Privacy Risks of IFTTT Recipes. Milijana Surbatovich, Jassim Aljuraidan, Lujo Bauer, Anupam Das and Limin Jia. International World Wide Web Conference (WWW), 2017.
- Assisting Users in a World Full of Cameras: A Privacy-aware Infrastructure for Computer Vision Applications. Anupam Das, Martin Degeling, Xiaoyou Wang, Junjue Wang, Norman Sadeh and Mahadev Satyanarayanan. Workshop on the Bright and Dark Sides of Computer Vision: Challenges and Opportunities for Privacy and Security (CV-COPS, co-located with IEEE CVPR), 2017.
- Towards Privacy-Aware Smart Buildings: Capturing, Communicating, and Enforcing Privacy Policies and Preferences. Primal Pappachan,, Martin Degeling, Roberto Yus, Anupam Das, Sruti Bhagavatula, William Melicher, Pardis Emami Naeini, Shikun Zhang, Lujo Bauer, Alfred Kobsa, Sharad Mehrotra, Norman Sadeh and Nalini Venkatasubramanian. International Workshop on the Internet of Things Computing and Applications (IoTCA, co-located with ICDCS), 2017.
Online Tracking
When we interact with the Web, we leave behind traces of our interactions, called digital footprints. These footprints reveal a lot about ourselves; our identity, habits, and desires. Such intensely personal information has great commercial value to advertisers in the form of serving targeted ads, but at the same time, it can also be misused by employers and repressive governments. To protect users, privacy tools such as ad- and tracker-blocking extensions have been developed. In turn, advertisers have begun leveraging more advanced tracking techniques that reduce the effectiveness of these approaches. In my research, I look at emerging techniques to track users and devices online, as well as ways to develop usable countermeasures.
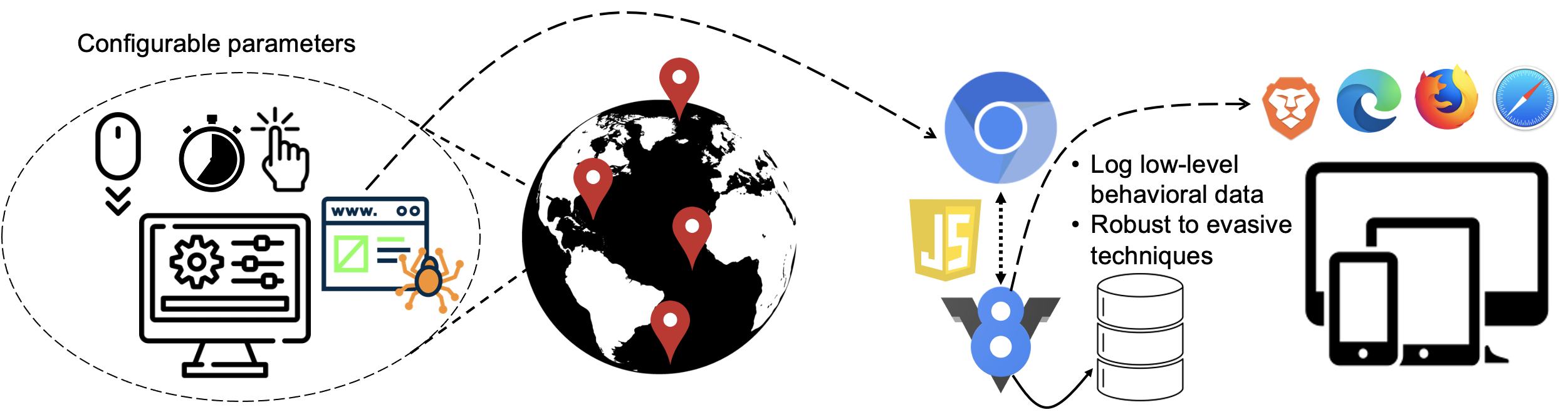
Relevant publications:
- JSHint: Revealing API Usage to Improve Detection of Malicious JavaScript. Shaown Sarker, Aleksandr Nahapetyan, Anupam Das, and Alexandros Kapravelos. Proceedings of the 27th Information Security Conference (ISC), 2024.
- Automated Generation of Behavioral Signatures for Malicious Web Campaigns. Shaown Sarker, William Melicher, Oleksii Starov, Anupam Das, and Alexandros Kapravelos. Proceedings of the 27th Information Security Conference (ISC), 2024.
- Comparative Privacy Analysis of Mobile Browsers. Ahsan Zafar and Anupam Das. Proceedings of the 13th ACM Conference on Data and Application Security and Privacy (CODASPY), 2023.
- Analyzing the Impact and Accuracy of Facebook Activity on Facebook's Ad-Interest Inference Process. Aafaq Sabir, Evan Lafontaine and Anupam Das. Proceedings of the 25th ACM Conference On Computer-Supported Cooperative Work And Social Computing (CSCW), 2022.
- Understanding the Privacy Implications of Adblock Plus’s Acceptable Ads. Ahsan Zafar, Aafaq Sabir, Dilawer Ahmed and Anupam Das. ACM ASIA Conference on Computer and Communications Security (ASIACCS), 2021.
- The Web’s Sixth Sense: A Study of Scripts Accessing Smartphone Sensors. Anupam Das, Gunes Acar, Nikita Borisov and Amogh Pradeep. ACM Conference on Computer and Communications Security (CCS), 2018.
- Every Move You Make: Exploring Practical Issues in Smartphone Motion Sensor Fingerprinting and Countermeasures. Anupam Das, Nikita Borisov and Edward Chou. Privacy Enhancing Technologies Symposium (PETS), 2018.
- Tracking Mobile Web Users Through Motion Sensors: Attacks and Defenses. Anupam Das, Nikita Borisov and Matthew Caesar. Network and Distributed System Security Symposium (NDSS), 2016.
- Do You Hear What I Hear? Fingerprinting Smart Devices Through Embedded Acoustic Components. Anupam Das, Nikita Borisov and Matthew Caesar. ACM Conference on Computer and Communications Security (CCS), 2014.
Password Analysis
Today’s Internet services rely heavily on text-based passwords for user authentication. The pervasiveness of these services, coupled with the difficulty of remembering large numbers of secure passwords, tempts users to reuse or modify existing passwords at multiple sites. My research looks at analyzing and identifying different ways in which users reuse or modify passwords using real-world, large-scale leaked data sets.
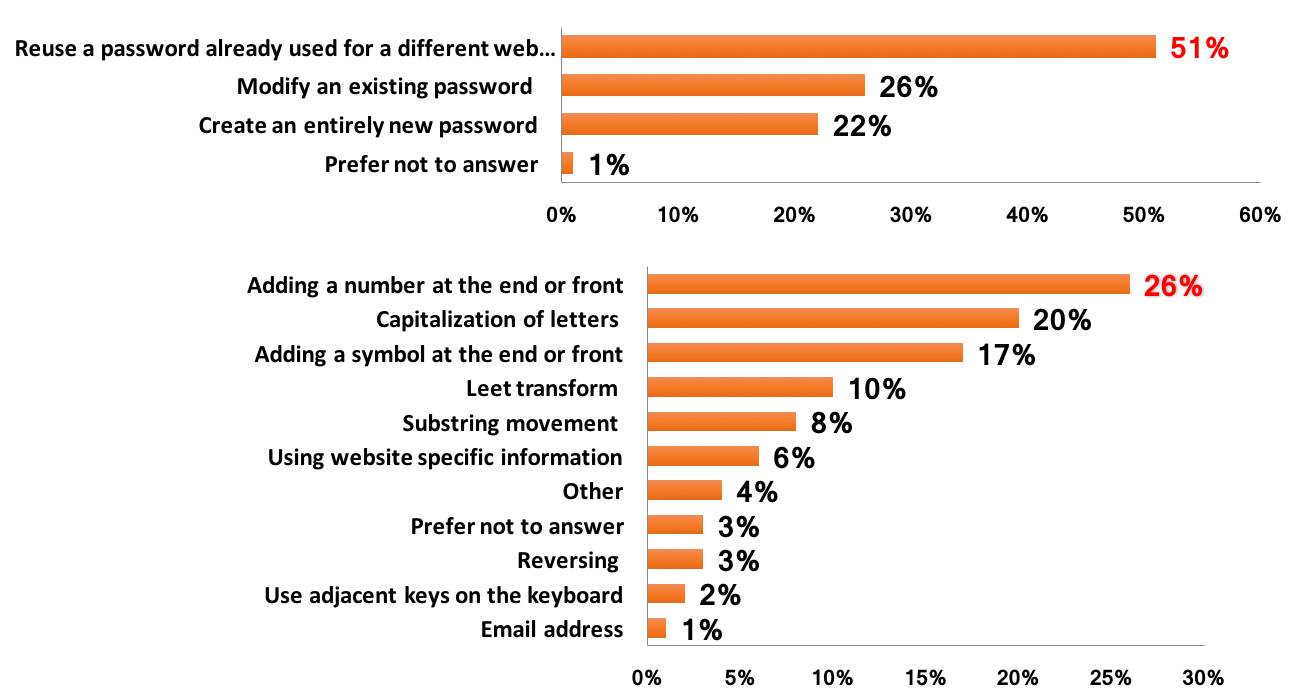
Relevant publications:
- The Tangled Web of Password Reuse. Anupam Das, Joseph Bonneau, Matthew Caesar, Nikita Borisov and XiaoFeng Wang. Network and Distributed System Security Symposium (NDSS), 2014.
- Password Correlation: Quantification, Evaluation and Application. Shouling Ji, Shukun Yang, Anupam Das, Xin Hu and Raheem Beyah. IEEE International Conference on Computer Communications (INFOCOM), 2017.
Securing Anonymity Networks (Tor)
Many people use anonymity networks like Tor to hide their digital footprints on the Internet. My research looks at analyzing the security and privacy guarantees provided by Tor in the presence of active and passive attackers.
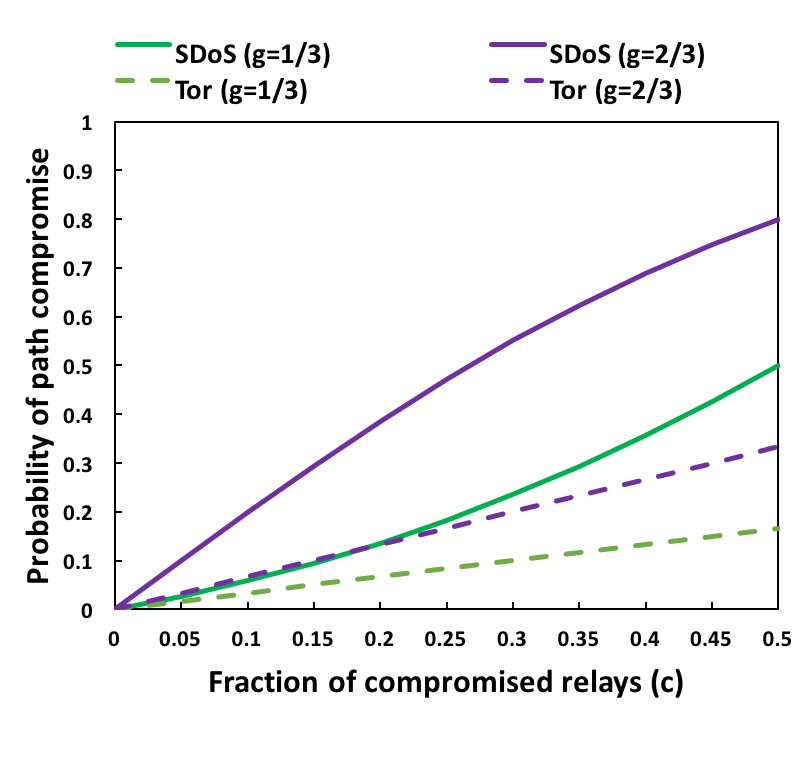
Relevant publications:
- Defending Tor from Network Adversaries: A Case Study of Network Path Prediction. Joshua Juen, Aaron Johnson, Anupam Das, Nikita Borisov and Matthew Caesar. Privacy Enhancing Technologies Symposium (PETS), 2015.
- Re^3: Relay Reliability Reputation for Anonymity Systems. Anupam Das, Nikita Borisov, Prateek Mittal and Matthew Caesar. ACM Symposium on Information, Computer and Communications Security (ASIA CCS), 2014.

- Analyzing an Adaptive Reputation Metric for Anonymity Systems. Anupam Das, Nikita Borisov and Matthew Caesar. Symposium and Bootcamp on the Science of Security (HotSoS), 2014.
- Securing Anonymous Communication Channels under the Selective-DoS Attack. Anupam Das and Nikita Borisov. International Conference on Financial Security and Data Security (FC) 2013.